Information Security
Our Information Security practice assists clients with clearing the clutter associated with what is proper information security versus just "checking" a box. Checking a box might help pass an audit but it will not keep a secure environment and moreover might instill the false sense of security.
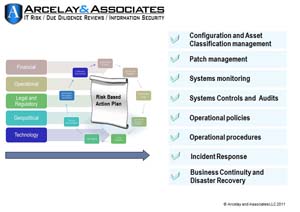
Properly implemented, Information Security is a never ending program with feedback loops covering: Governance, Risk, Policies, Assets, Human Resources, Access Controls, Physical, Logical and Environmental considerations, Information Systems life cycle, Incident Management and Compliance. These elements consider operational input from monitoring processes and validated alerts issued by access and identity management, work place security, applications and data security, and systems and network security.
While we leverage our Information Security expertise and apply our expert knowledge in: Vulnerability Detection, Threat Detection, Threat and Vulnerability Remediation, Incident Response programs, Application Triage, Logging and monitoring, and Encryption and Architecture Design, each program solution we device is tightly fitted and integrated with the organization we partner with.